Windows Azure Multi Factor Authentication is a great service/Product that gives you a complete MFA solution both on premise and in the cloud. The best thing is that as of yesterday, it’s free for all accounts and not just for admin accounts.
Now you don’t have any excuses to not secure your admin accounts that have potentially access to multiple thousands of email accounts and other sensitive information.
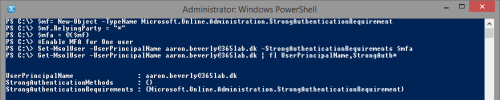
One thing that I have not been testing until today, was to activate MFA for a Federated Administrator(DirSynced account with global administrator rights).
It works completely transparent for the user/admin, they just log on as they normally do to the ADFS server, and then the Azure MFA will kick in and require additional authentication.
How awesome is that?
Here’s how to activate MFA for an admin user (regardless if you’re using ADFS or not):
1. Logon to the O365-portal, under users and groups, find the “Set Multi-factor authentication requirements” row and click “Set up”.

2. Choose the account(s) that you want to enable MFA for and click enable and then enable MFA.


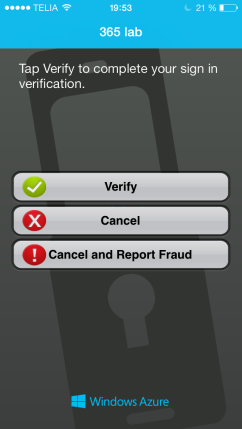
3. After activated MFA, at next logon, the admin have to put in additional info about the second factor of authentication preferred. See the process to enroll devices as follows.

Personally, I prefer using the mobile app as a second factor of authentication since its the easiest method, but it’s also possible to use text messages and phone for that.

After verifying the activation with the Multi Factor Authentication app in my phone, I’m almost set, apart from one thing.
If you indend to use this account to connect to Office 365 with Outlook or ActiveSync, you will also need to create one or more app passwords that will be static passwords that can be used in cases where MFA doesn’t work.

After creating eventual app passwords, you have now configured the specific account for multi factor authentication. Note that Microsoft is planning to add native multi-factor authentication for applications such as Outlook, Lync, Word, Excel, PowerPoint, PowerShell, and OneDrive for Business, with a release date planned for later in 2014.
Was it Hard? – No!
Should you use it whenever possible? – Yes!
Now, what’s your excuse to not activate Windows Azure Multi Factor Authentication for your Admin accounts?
/Johan