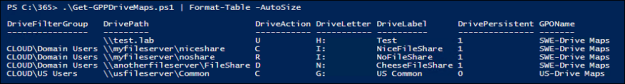
In addition to my earlier creations that gives you an inventory of your GPO Deployed Printers and GPP Drive Maps, I’ve now created a similiar script that makes inventory of WSUS settings in all your GPO’s.
This can very much come in handy when having an extensive amount of GPO’s that are controlling WSUS settings (e.g. for different maintenance schedules).
See the example below of the output:

<#
.SYNOPSIS
Function that find certain information about all your WSUS related GPO's.
.NOTES
File Name: Get-GPOWsusInfo
Author : Johan Dahlbom, johan[at]dahlbom.eu
The script are provided “AS IS” with no guarantees, no warranties, and it confer no rights.
Blog : 365lab.net
#>
function Get-GPOWsusInfo {
try
{
Import-Module GroupPolicy -ErrorAction Stop
}
catch
{
throw "Module GroupPolicy not Installed"
}
$GPO = Get-GPO -All
foreach ($Policy in $GPO){
$GPOID = $Policy.Id
$GPODom = $Policy.DomainName
$GPODisp = $Policy.DisplayName
[xml]$xml = Get-GPOReport -Id $GPOID -ReportType xml
$GPOSec = Get-GPPermissions -All -Guid $GPOID
$WSUSBase = Get-GPRegistryValue -Guid $GPOID -Key HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate -ErrorAction SilentlyContinue
$WSUSAU = Get-GPRegistryValue -Guid $GPOID -Key HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU -ErrorAction SilentlyContinue
if ($WsusBase) {
New-Object PSObject -Property @{
GPOName = $GPODisp
GPOLinks = $xml.gpo.Linksto.SOMPath
GPOFilter = ($GPOSec | Where-Object {$_.Permission -eq "GpoApply"}).trustee.name
ScheduleDay = ($WSUSAU | Where-Object {$_.ValueName -eq "ScheduledInstallDay"}).Value.tostring().Replace("0","0 - Every Day").Replace("1","1 - Sunday").Replace("2","2 - Monday").Replace("3","3 - Tuesday").Replace("4","4 - Wednesday").Replace("5","5 - Thursday").Replace("6","6 - Friday").Replace("7","7 - Saturday")
Installtime = ($WSUSAU | Where-Object {$_.ValueName -eq "ScheduledInstallTime"}).Value.tostring() + ':00'
AutoUpdateSetting = ($WSUSAU | Where-Object {$_.ValueName -eq "AUOptions"}).Value.tostring().Replace("2","2 - Notify for download and notify for install").Replace("3","3 - Auto download and notify for install").Replace("4","4 - Auto download and schedule the install").Replace("5","5 - Allow local admin to choose setting")
WSUSTargetGroup = ($WSUSBase | Where-Object {$_.ValueName -eq "TargetGroup"}).Value
WSUSServer = ($WSUSBase | Where-Object {$_.ValueName -eq "WUServer"}).Value
}
}
}
}
Hope you find this useful!
When I find the time I’ll create a more complete set of GPO reporting functions with more functionality than they have today, maybe with help from Ramblingcookiemonster that has extended and created additions to the GP Preferences functions.
Until next time, Happy GPO Reporting!
/Johan