Lately I’ve been doing quite a few Hybrid setups.
One of the things that cause quite a lot of pain when doing migrations in general is getting information out to your users.
Even if you have a good communication plan, only 20% of your users read the information and only 5% of them reflect and understand it. 🙂
To make this a bit easier, I’ve created a small script that starts Hybrid migration batches and sends out information to the end user.
This is of course just an example, but gives you a good idea of what you are able to do with quite simple means.
Getting started:
- Review all relevant variables in the script
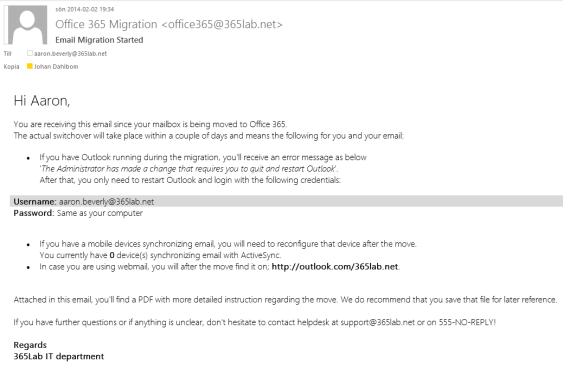
- Change the text in BodyHybrid.txt to fit in to your needs, the html in that file will be the information sent in the email. The words ActiveSyncDevices,OWAAddress,EmailAddress and Firstname will automatically be replaced by its corresponding variables. (and no the css is not the best 🙂 )
- Create the PDF Office365Info.pdf and put it in the same folder as the script, that file will be attached to the email.
- Create input file Prepare-Mailboxes.csv with samAccountNames of the users that you want to migrate. (Note that I am assuming that the users Email Address and UserPrincipalName are the same in the script)
Also note that the MoveRequest settings in the script might not fit your needs (Baditemlimit, Largeitemlimit).
As we are using the switch -SuspendWhenReadytoComplete in the script, the batches will autosuspend at 95% completion.
That means you’ll have to complete them manually with for example the following line:
Get-CloudMoveRequest | Where-Object {$_.Status -eq "AutoSuspended"} | Resume-CloudMoveRequest.
Another good option to get in better control of your remote mailbox moves is to use Michael Halls excellent tool based on PowerShell and Excel that does that for you.
Start-HybridMigrations.ps1
<#
.SYNOPSIS
Starts hybrid migrations based on input (samAccountName) from a csv file.
.DESCRIPTION
The script starts hybrid migrations and sends out information emails based on the file "BodyHybrid.txt".
PowerShell V3.0 required
.NOTES
File Name: Start-HybridMigrations.ps1
Author : Johan Dahlbom, johan[at]dahlbom.eu
The script are provided “AS IS” with no guarantees, no warranties, and they confer no rights.
#>
#Import Required Modules
Import-Module ActiveDirectory
#Define Mail Information and Logging
$Users = Get-Content Prepare-MailboxMoves.csv
$BodyHybrid = Get-Content BodyHybrid.txt -Raw
$OWAAddress = 'http://outlook.com/365lab.net'
$Attachment = Get-Childitem .\Office365Info.pdf
$PSScriptRoot = Split-Path -Parent -Path $MyInvocation.MyCommand.Definition
$Logfile = ($PSScriptRoot + "\HybridMigrations.log")
#Define Exchange Online Variables
$ExchServ = "exchangecas.corp.365lab.net"
$HybridServer = "webmail.365lab.net"
$DeliveryDomain = "365lab.mail.onmicrosoft.com"
$OnPremiseUsername = "cloud\svc_mailmigration"
$OnPremisePassword = ConvertTo-SecureString "password" -AsPlainText -Force
$CloudUsername = "svc-cloudmigration@365lab.onmicrosoft.com"
$CloudPassword = ConvertTo-SecureString "password" -AsPlainText -Force
$CloudCred = New-Object System.Management.Automation.PSCredential $CloudUsername, $CloudPassword
$OnPremCred = New-Object System.Management.Automation.PSCredential $OnPremiseUsername, $OnPremisePassword
#Connect to OnPremise Exchange
if (!(Get-Command Get-ActiveSyncDeviceStatistics -ErrorAction SilentlyContinue)) {
try {
Add-PSSnapin Microsoft.Exchange.Management.PowerShell.E2010
} catch {
$Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri "http://$ExchServ/powershell" -Authentication Kerberos
Import-PSSession -Session $Session -CommandName Get-ActiveSyncDeviceStatistics -FormatTypeName * | Out-Null
}
}
#Connect to Exchange Online
if (!(Get-Command New-CloudMoveRequest -ErrorAction SilentlyContinue))
{
$session = New-PSSession -ConfigurationName Microsoft.Exchange -Authentication Basic -ConnectionUri https://ps.outlook.com/powershell -AllowRedirection:$true -Credential $CloudCred
Import-PSSession $session -Prefix Cloud
}
function LogWrite {
Param ([string]$Logstring)
Add-Content $Logfile -value $logstring -ErrorAction Stop
Write-Host $logstring
}
function Send-MigrationMail {
param(
[Parameter(Mandatory=$true)]
[string]$Message,
[Parameter(Mandatory=$true)]
[string]$Recipient
)
$emailFrom = "Office 365 Migration <office365@365lab.net>"
$smtpserver = "smtpyrelay.365lab.net"
$subject = "Email Migration Started"
$cc = "migrator@365lab.net"
Send-MailMessage -From $emailfrom -To $Recipient -Cc $cc -SmtpServer $smtpserver -Subject $subject -Body $Message -BodyAsHtml -Attachments $Attachment
}
LogWrite "$(get-date -Format u)"
foreach($aduser in $users) {
$emailAddress = (Get-ADuser $aduser -properties UserPrincipalName).UserPrincipalName
$firstname = (Get-ADuser $aduser).givenname
#Find the number of Active ActiveSyncDevices that the user have in the local Exchange solution. If not, set to 0.
$ActiveSyncDevices = (Get-ActiveSyncDeviceStatistics -Mailbox $aduser | Where-Object {$_.LastSuccessSync -gt (Get-Date).AddDays(-30)}).count
if (!($ActiveSyncDevices)) {
$ActiveSyncDevices = "0"
}
#Start Email Migration for user
try {
New-CloudMoveRequest -Identity $emailaddress -Remote -RemoteHostName $HybridServer -RemoteCredential $OnPremCred -TargetDeliveryDomain $DeliveryDomain -BatchName $emailAddress -SuspendWhenReadyToComplete -BadItemLimit 50 -LargeItemLimit 50
} catch {
$err = $_
Logwrite "ERROR: Failed to start migration on $($emailAddress)`r`n$($err)"
}
#Verify that the move request was successful and send information email
if ((Get-CloudMoveRequest | Where-Object {$_.BatchName -eq $emailAddress} -ErrorAction SilentlyContinue)) {
LogWrite "INFO: Started migration of user $($emailAddress) $(get-date -format u)"
Send-MigrationMail -Recipient $emailAddress -Message $BodyHybrid.Replace('firstname',"$firstname").Replace('ActiveSyncDevices',"$ActiveSyncDevices").Replace("emailaddress","$emailaddress").Replace("OWAAddress","$OWAAddress")
}else{
LogWrite "ERROR: Could not start migration for user $($emailAddress), please verify that user exists"
}
}
The script would of course be possible to extend with lots of things like license assignment, watching the mailboxes as they move and lots and lots of other things, but that’s for another day.
Just let me know if you have suggestions on improvements or other things that should be changed.
Download the script complete with the HTML-template and example csv file from here.
Happy migrations!
/Johan