While implementing Lync Online at a customer a while ago, I ran in to a small, but for the end-users, quite annoying issue. The sign-in address was not automatically populated in the Lync Client at first sign on, which means they had to put in their email address/sip address at first logon. Since both Dirsync and ADFS was in place, auto-populated username would mean SSO for the users, which of course is something you always want.
SOLUTION(s)
After doing some research, it turned out that the Lync/SfB Client is getting the sign-in address from the proxyAddresses or msRTCSIP-PrimaryUserAddress (requires Lync/SfB ad schema extensions) attributes.
In order to solve the issue, you need to follow one of the approaches below. The first one is the recommended one since it doesn’t require you to extend your AD schema, but the second one might be good to have as a reference.
APPROACH #1 – Populate the proxyAddresses attribute
With this approach, we simply populate the proxyAddresses attribute with the corresponding sip/email address with a SIP: prefix. In my example below, I am assuming that your email/sip address is the same as the UPN on your users.
#Import Active Directory Module
Import-Module -Name ActiveDirectory
#Loop through all users with 365lab.net as UPN domain
Get-ADUser -Filter {userprincipalname -like "*365lab.net"} | ForEach-Object -Process {
#Construct SIP address based on UPN
$SIPAddress = "SIP:{0}" -f $_.UserPrincipalName
#Populate the msRTCSIP-PrimaruUserAddress attribute with the constructed SIP Address
Set-ADUser -Identity $_.SamAccountName `
-Add @{"proxyAddresses"=$SIPAddress}
}
Verify that your users have got the proper address with the attribute editor, as below:

APPROACH #2 – Extend the AD schema and populate the msRTCSIP-PrimaryUserAddress attribute
Please note that this requires you to extend your Active Directory schema with extensions from the Lync Server installation. If you’re not familiar with schema extensions, please consult someone with that experience!
1. Download the .ldf schema extension files from my OneDrive here (at your own risk), or download a Lync Server 2013 installation media for example from here. You will find the required .ldf-files in the \Support\Schema folder on the .iso file as below.

2. Import the schema files using ldifde.exe from your schema master domain controller (as per instructions on http://technet.microsoft.com/en-us/library/gg398607.aspx) in the following sequence (Important!). The changes must of course be performed by a Schema Admin, in an elevated command prompt.
- ExternalSchema.ldf
ldifde -i -v -k -s DC1 -f ExternalSchema.ldf -c DC=X "DC=contoso,DC=com" -j C:\LogFileFolder
- ServerSchema.ldf
ldifde -i -v -k -s DC1 -f ServerSchema.ldf -c DC=X "DC=contoso,DC=com" -j C:\LogFileFolder
- BackCompatSchema.ldf
ldifde -i -v -k -s DC1 -f BackCompatSchema.ldf -c DC=X "DC=contoso,DC=com" -j C:\LogFileFolder
- VersionSchema.ldf
ldifde -i -v -k -s DC1 -f VersionSchema.ldf -c DC=X "DC=contoso,DC=com" -j C:\LogFileFolder
In my example below, the domain name is lucernepublishing.local/LUCERNE and the schema master DC is LUC-DC1.
After a successful schema update, you should be able to see the required attribute on a user as below:
3. Populate the msRTCSIP-PrimaryUserAddress attribute for all Lync enabled users. The attribute shall be populated just as it would be in a regular Lync environment, (example: sip:aaron.beverly@365lab.net). In order to automate this you could use my powershell script below. In the script I am assuming that your UserPrincipalName matches your SIP address (which is usually the case, at least when using Office 365).
#Import Active Directory Module
Import-Module -Name ActiveDirectory
#Loop through all users with 365lab.net as UPN domain
Get-ADUser -Filter {userprincipalname -like "*365lab.net"} | ForEach-Object -Process {
#Construct SIP address based on UPN
$SIPAddress = "SIP:{0}" -f $_.UserPrincipalName
#Populate the msRTCSIP-PrimaruUserAddress attribute with the constructed SIP Address
Set-ADUser -Identity $_.SamAccountName `
-Replace @{"msRTCSIP-PrimaryUserAddress"=$SIPAddress}
}
After running the script, all users in scope will have their msRTCSIP-PrimaryUserAddress populated.

RESULTS
The result we get after updating the attribute(s), is that we now have a properly populated username when starting our Lync client the first time.
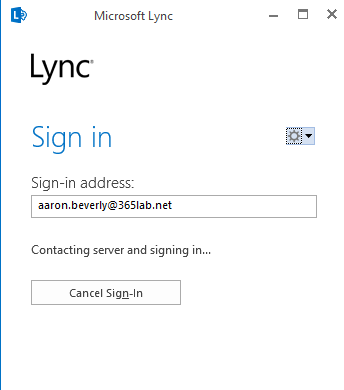
If you have questions or suggestions regarding the post, let me know!
/Johan